Cybersecurity Services for Healthcare
10,000+
1000
15000
1000
80000
Key Offerings
- Health Data Privacy and Protection
- Medical Device Security
- Risk and Governance
- Infra Security
- Cloud Security
- Digital Identity
- Application Security
Our Health Data Privacy and Protection services help enterprises meet security and privacy objectives through policy definition, development, and monitoring of the end-to-end risk management program. We implement:
- Controls for data protection
- Competency based training and awareness programs
- Privacy control procedures
We assess the potential risk and impact of a medical device by thoroughly reviewing the technologies used and the maturity of processes run throughout its lifecycle. We then develop a tailored remediation roadmap, build key controls, and provide remediation services end-to-end across device firmware, network segmentation, etc.
We have extensive experience and expertise in the field of governance, risk, and compliance. Our seasoned practitioners provide strategic insights and advisory services to tackle risk and compliance challenges across the enterprise.
We offer comprehensive services for infrastructure security that help defend against cyberattacks on infrastructure and respond to threats in real time. We help customers enhance their cyber defense by bringing cybersecurity skills at scale and deploying best in class protection controls and operational capabilities.
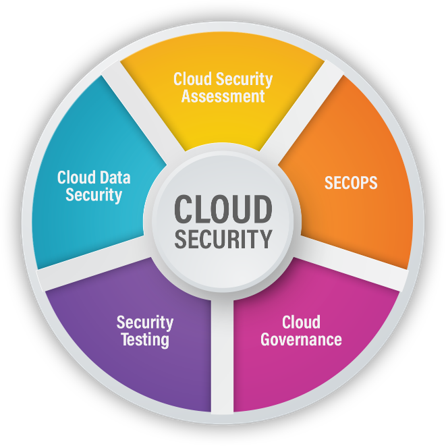
Our cloud security and compliance framework and rich experience empower organizations to use cloud environments without the fear of data breaches or regulatory lapses. Our services are aligned with industry best practices and proven security services delivery models. We help:
- Manage cloud security risks
- Build security defense on the cloud
- With expertise across major public cloud platforms
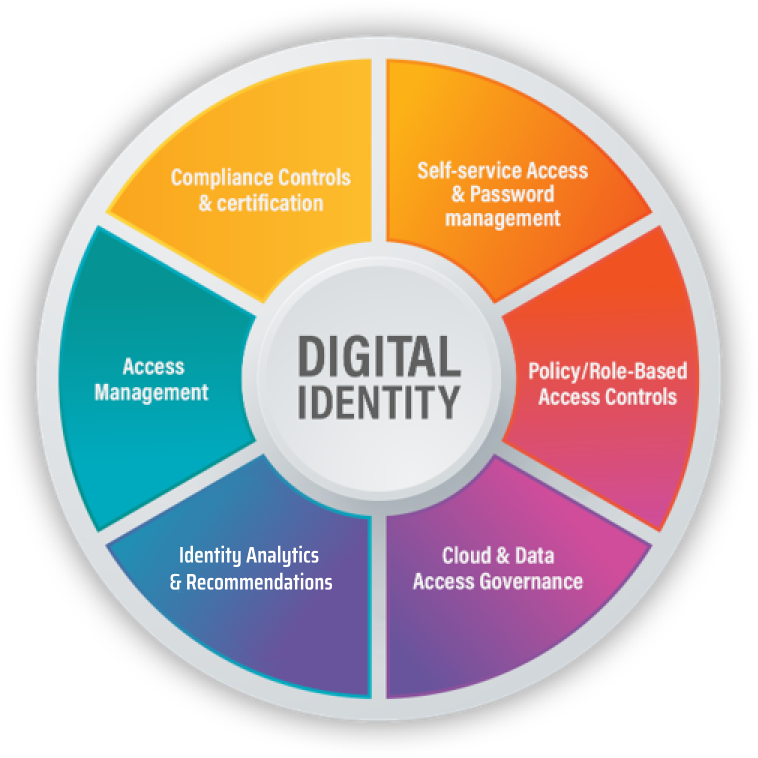
Our digital identity experts help transform business processes and user experience through agile identity and access management services. We help in delivering successful digital identity programs for healthcare companies of all sizes and types.
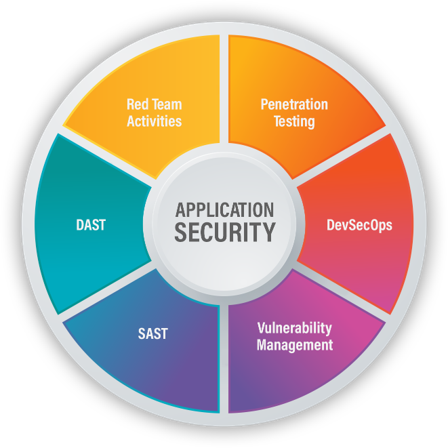
Our application security services are robust, scalable, and business-centric. They seamlessly align with the dynamics of application development. Equipped with the right methodologies to effectively identify and remediate vulnerabilities, we securely build and deploy applications anywhere with focus on the 3 pillars – people, process, and technology.